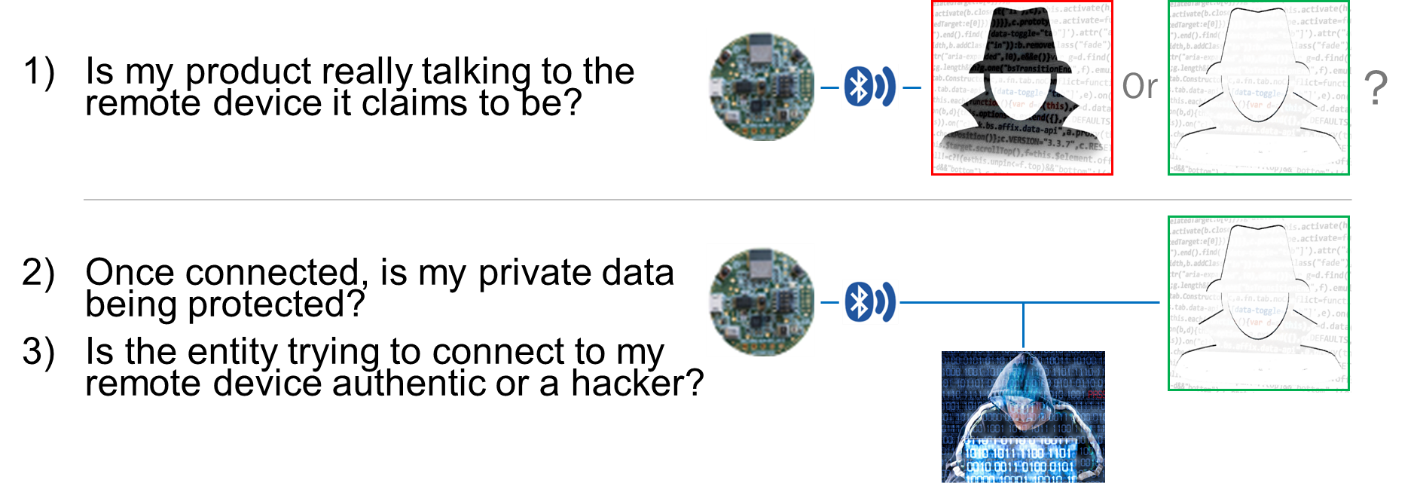
Many devices at the edge of the IoT rely on processors alone to manage critical functions or to collect sensitive data, and this fact is not lost on the hacker community. Unfortunately, there are several recent examples of security breaches where the entry point was one of these unsecured, low-level IoT processors connected to a larger network. Attackers use these unsecured devices as an entry point to the larger network where they are then free to explore and harvest a accompany's assets or alter the performance of other devices on the network. The risks to systems and businesses are enormous. As a result, securing these devices by implementing future-proof security tools that are fast, small, and of course secure, is imperative for implementing a security strategy that encompasses all connected devices. We recently partnered with ON Semiconductor to address the security needs of the RSL10, a flexible multi-protocol System on Chip (SoC) that brings ultra-low-power Bluetooth Low Energy to many applications. Some of the security scenarios that we looked to address are:
Figure 1. IoT Security Concerns
The ON Semiconductor RSL10 radio family that brings ultra-low-power Bluetooth 5 capability to wireless applications. The SoC is ideal for many IoT applications and many users will likely require additional features such as device-to-device security and/or data protection. Implementing these security features can ensure an RSL10 device is really talking to the authorized remote device it is expecting. Or once the device is connected, features that ensure the private data is protected during transmission and the request for data is coming from an authenticated entity. Veridify Security's public key methods authentication and data protection, as well as support for DOME™, Veridify's zero-touch onboarding, blockchain ownership management, and enrollment solution.
Veridify’s security solutions can be implemented in software-only (for example, running on the RSL10’s Arm® Cortex®-M3 processor) and require little memory, making them easy to employ and well-suited for IoT applications in the industrial, medical, automotive, and consumer spaces.
As an ON Semiconductor Cybersecurity Ecosystem partner, Veridify Security provides turnkey security solutions, which helps to accelerate secure RSL10 product development.
RSL10 Security Solution
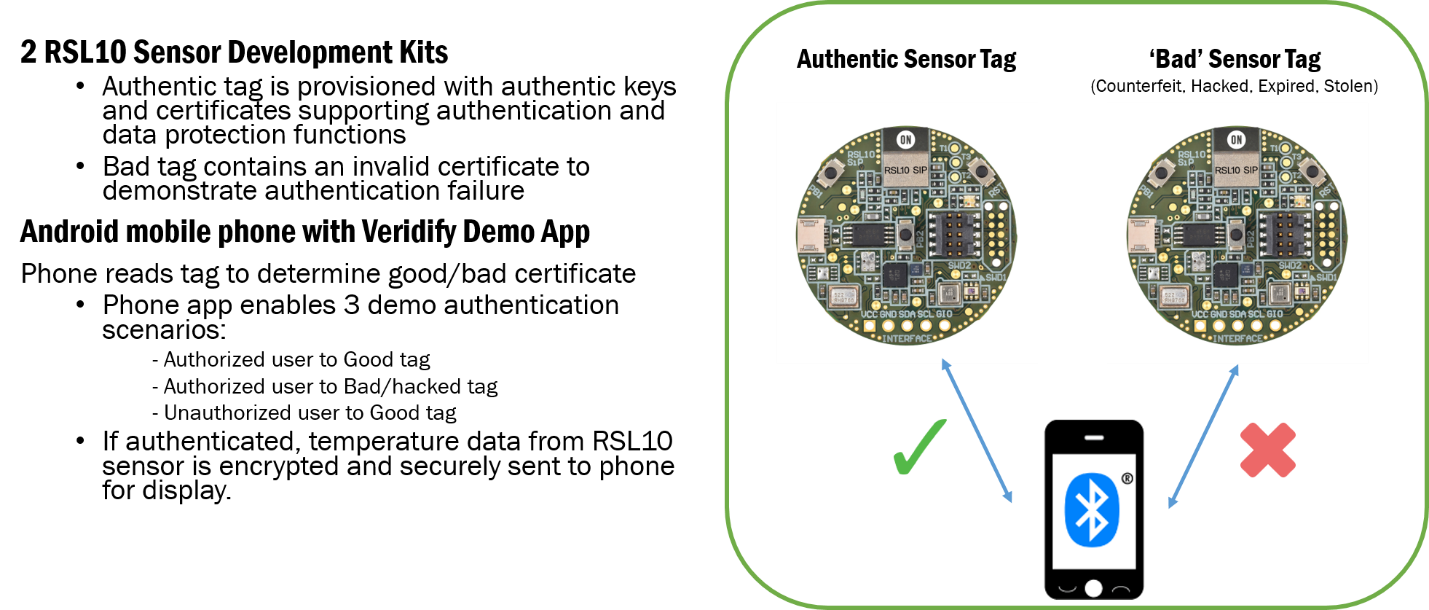
Figure 2. RSL10 Security Solution with Veridify
The companies have created a demonstration showing how Veridify Security’s methods can be leveraged to easily implement device-to-device security on the RSL10 Bluetooth Low Energy SoC. The demo uses an RSL10 sensor board programmed with Veridify’s security methods, mutually authenticating with a smartphone over Bluetooth Low Energy. If both endpoints (phone and sensor) are authentic, real-time temperature data collected by the RSL10 will be encrypted and transmitted to the phone for display. A counterfeit tag and unapproved user are also provided to show how the system can identify bad sensors and unauthorized users. The demo shows that by using Veridify Security’s software, it is easy to secure IoT edge devices based on RSL10.
Veridify Security tools now available via CMSIS-pack for RSL10
Veridify Security tools are ISO 26262 ASIL D certified and are now available for the RSL10 in the form of a CMSIS pack providing developers with a familiar interface for easy implementation. Implementing powerful security applications like device-to-device authentication, data protection, and the secure firmware update is now easier than ever.
The Bluetooth IoT Development Kit CMSIS-Pack containing Veridify’s Public Key security tools is now available for free download here!
Be sure to subscribe to our blog and follow us on social media to receive the latest updates on our technologies, solutions and company news!
Twitter | Facebook | LinkedIn | Instagram | YouTube